Big Hack Attack: Anti-Trump Tweet Sent From McDonald's Account
- by Joe Mandese @mp_joemandese, March 16, 2017

McDonald’s has come under attack after its corporate account tweeted an anti-Trump message that the company said was the result of a hack.
“Twitter notified us that our account was compromised. We deleted the tweet, secured our account and are now investigating this,” the fast-food marketer tweeted in response to the incident, the latest in a flurry of brand-related assaults involving President Donald Trump and big consumer marketers, as well as hacking.
Though the rogue tweet was deleted on McDonald’s Twitter account, copies of it continue to circulate via screen grabs tweeted by other
users on the micro blogging platform.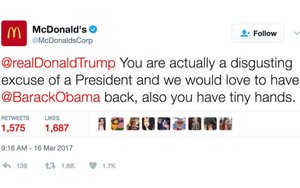
“@realDonaldTrump You are actually a disgusting excuse for a President and we would love to have @BarackObama back, also you have tiny hands,” reads a screenshot of the McDonald’s corporate tweet posted by one user that cites 1,575 retweets at that time of that retweet.
Whether the fast-food giant was culpable or not, the incident set off a tweetstorm of activity from Trump supporters tweeting calls for a McDonald’s boycott over it.advertisement
advertisement
Initially, the sentiment of Twitter users was overwhelmingly negative toward McDonald's following the tweet, but as the day progressed, it became more split.
By late Thursday, the sentiment of Twitter users was 14.44% negative vs. 13.96% positive, according to an analysis by social analytics firm Synthesio.
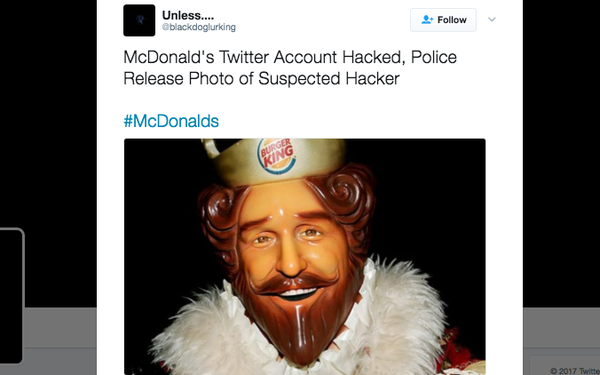
One of the most popular tweets following the incident featured a picture of Burger King’s king character, accompanying the tweet, “McDonald's Twitter Account Hacked, Police Release Photo of Suspected Hacker”





I won't be surprised if the comment about Trump's tiny hands brings a revival of the photos of his [purported] naked jewels tweeted last year.