Barracuda Warns Of New Email Phishing Threat
- by Ray Schultz , April 10, 2018

Barracuda has identified a new phishing threat: a Quant Loader Trojan that could distribute ransomware and steal passwords. Unknowing email users could easily be victimized, it warns.
The campaign has consisted of several mini-campaigns, each lasting less than day, Barracuda states. These efforts rely on “an email content and file name pattern (with some emails having no text content and only a subject line).”
The emails come from a single domain serving “malicious script files over Samba, and a single variant of Quant being distributed from a handful of domains,” the company adds.
In one example, the Samba shares are “publicly accessible while still active,” Barracuda notes. Attempts to access the URLS via HTTP has at times led to redirects. The result is that a random key generator file is downloaded. On a positive note, these attempts are flagged as malicious by most anti-virus software.
Sold on underground forums, Quant Loader allows bad actors to configure the payload upon infection with a management panel. This type of configurable malware is increasingly being offered for sale, allowing malware development to be separated from distribution, Barracuda says.
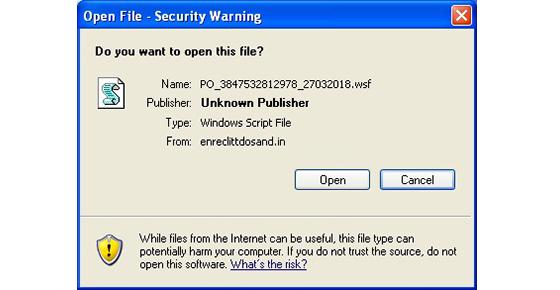
Barracuda warns that an unfamiliar file extension — especially when compressed in a ZIP file — is a likely sign of a malware outbreak.
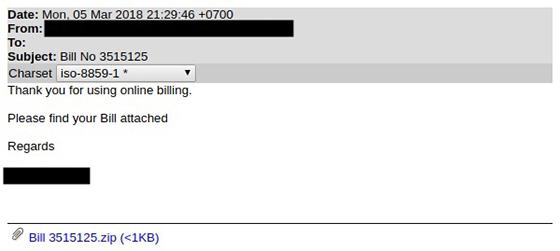
This was the case last month when a “.url” file extension appeared in emails purporting to be billing documents. These shortcut files mostly use a “variation on the CVE-2016-3353 proof-of-concept, containing links to JavaScript files (and more recently Windows Script Files).”
But the new threat rely on a URL that is “prefixed with ‘file://’ rather than ‘http://; which fetches them over Samba rather than through a web browser,” Barracuda adds.
The result is that the contained code is executed with Wscript under the current user’s profile instead of requiring browser exploitation. Barracuda adds that the remote script files are “heavily obfuscated.”
In general, the new threat consists of these elements:
- Phishing — Emails sent to persuade the recipient to act on their requests.
- Social Engineering — This occurs whenattackers engage with recipients to gain their trust and act on their malicious request.
- Exploitation — CVE-2016-3353 was used to circumvent the browser and execute malicious scripts in user-space.
- Obfuscation — Malicious scripts are heavily obfuscated to prevent or slow static analysis efforts.
Barracuda advises to provide regular security awareness training for employees.