 Researchers at Malwarebytes Labs have discovered another malvertising campaign, likely from the same group responsible for the recent attack on The Huffington Post and Zillow. An ad was
used to deliver the Cryptowall ransomware via an ad built in Flash.
Researchers at Malwarebytes Labs have discovered another malvertising campaign, likely from the same group responsible for the recent attack on The Huffington Post and Zillow. An ad was
used to deliver the Cryptowall ransomware via an ad built in Flash.
This new malicious campaign involves Google's DoubleClick ad network.
Jerome Segura, senior security researcher at
Malwarebytes, said the latest malvertising attack was carried through merchenta, a company that provides a platform for ad exchange and direct integrations with top publishers, according to
Malwarebytes. Merchenta boasts 28 billion monthly impressions in the U.S., 14 billion in the U.K., 18 billion in EMEA, and 9 billion in Asia. The company works with top-tier ad networks, such as
Google DoubleClick, and real-time bidding platform Biddable.
advertisement
advertisement
DoubleClick is not directly responsible for loading the malicious ad, but it starts the chain with publishers, which
unfortunately have little control over transactions that follow.
The criminals posed as an advertiser, infiltrating the platform via a third party and managed to house a malicious
advertisement directly on merchenta's ad platform that fed into Google's DoubleClick channels, according to Malwarebytes. Within minutes, the malicious ad had infected 95% of the ads running on the
network in United States, the United Kingdom and Europe, exposing a huge number of people worldwide.
The Flash ad hosts the malware. Using the ad will redirect to another page. In this case,
individuals do not need to click on the ad before infecting a computer. That's a big misconception. As the ad server loads the Web page on the individual's screen, the malware downloads the malicious
software onto the computer.
"We call it a drive-by download," said Segura. "You surf the Web, the ad loads on the screen, the computer gets infected. It happens within seconds."
The
latest example is another reminder of one of the weaknesses with online advertising. The biggest weakness involves ad networks relying on third-party "trustworthy" data. Vulnerabilities in Flash
technology present another problem, Segura said. The majority of ads use Flash, although some companies have begun building ads using HTML5. If the ad network can host the ad it becomes less of a
problem, he said.
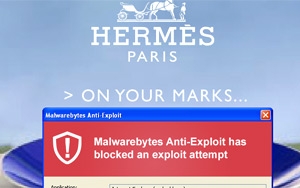
Malwarebytes worked with ClarityAd to confirm the malicious attack that began last weekend, which showed a well-known ad network with direct ties to Google's DoubleClick
being caught in a large malvertising incident. Several well-known sites were affected, such as Hermes Paris.
UPDATE: Neil McClements, merchenta CEO, disagrees. In an email he insists the
company has "zero tolerance for malware" and is working hard to prevent this type of disruption.