Commentary
What Hackers Do With 54B Leaked Cookies
- by Laurie Sullivan , Staff Writer @lauriesullivan, April 8, 2024
Marketers love first-party cookies because they remember visitor login details and personalize content, but there is a dark side to the cookies -- much darker than brands collecting personal consumer data just to follow prospective customers around the web.
First-party cookies are generally less intrusive than third-party cookies, but may pose much more serious security risks. That is because more than the personal data stored in them is at risk.
NordVPN, a virtual private network service, has found billions of ad-tracking cookies leaked on the dark web. Of the 54 billion cookies, at least 1.5 billion were from the United States and 24% were active.
The researchers at NordVPN analyzed the cookies and listings found for sale on the dark web to determine how they were stolen, what security and privacy risks they pose, and what kinds of information they contain. The study released Monday sheds light on how internet users endanger themselves by accepting cookies.
advertisement
advertisement
The most cookies came from Brazil, India, Indonesia, and Vietnam. The United States ranked No. 4 in terms of number of leaked cookies.
More than 2.5 billion of the cookies in the dataset were from Google, with another 692 million from YouTube. More than 500 million were from Microsoft and Bing.
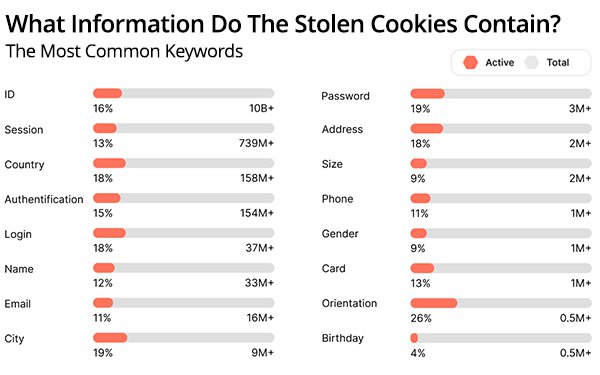
The largest keyword category -- “assigned ID,” at 10.5 billion -- is followed by “session ID” at 739 million. These cookies are assigned or connected to specific users to keep sessions active or identify them on the website to provide services. These were followed by 154 million authentication and 37 million login cookies.
These cookies leaked to the dark web also included names, email addresses, cities, passwords, and addresses. These were most common in the personal information category.
Adrianus Warmenhoven, security advisory board member at NordVPN, explains that without cookies, the server cannot verify the user. Once logged in with a password and multifactor authentication (MFA), the server gives the user a cookie, so when he/she comes back to the site with a cookie in the browser, the server recognizes the cookie and knows the user has already logged in.
“If this cookie is stolen and is still active, an attacker can potentially login into your account without having your password or needing MFA,” he said.
Up to 12 different types of malware were used to steal these cookies. Nearly 56% were collected by Redline, a popular infostealer and keylogger.
According to the study, Redline is advertised as malware as a service for $100 per month. It includes modules for customization and extra features, like downloading other malware.
Sexual orientation, although less frequent, appeared 500,000 times in the dataset, with a higher rate of active cookies, about 26%.
The report also notes that in some countries exposing this online could add risks for members of the LGBTQ+ community. Having someone’s non-traditional sexual orientation exposed could lead to severe consequences.
Redline, per the study, is advertised as malware as a service for $100 per month. It includes modules for customization and extra features, like downloading other malware.



