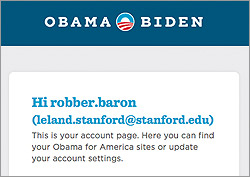
Web sites run by the campaigns of Barack Obama and Mitt Romney are "leaking" usernames and other potentially identifiable data, according to a new report by Stanford grad
student Jonathan Mayer.
"The major presidential campaigns both fell short of best practices in their Web site design and testing," Mayer wrote Thursday in a blog post outlining his findings.
Mayer reports that referrer
headers on several pages from the site BarackObama.com include the usernames of people who have registered with the site. Those usernames consist of a Facebook name (with the first and last name
separated by a dot), or the first part of an email address (before the @ symbol).
advertisement
advertisement
Referrer headers on several pages from MittRomney.com also include names, and in some cases, partial email
addresses and ZIP codes.
Those referrer headers can be seen by third parties that track visitors to the campaigns' sites. Mayer reports that 10 companies receive usernames from
BarackObama.com: Akamai, Amazon, BrightTag, Chartbeat, Facebook, Google, Hoefler & Frere-Jones, New Relic, Think Realtime, and Zendesk. He says 13 companies receive partial email addresses from
MittRomney.com: Adobe, Akamai, Amazon, Compete, comScore, Facebook, Google, Lotame, New Relic, Optimizely, Search Discovery, ShareThis, and Syncapse.
Both of the presidential campaigns
reportedly are undertaking extensive efforts to track and target potential voters who visit the official campaign sites. The New York Timesreported on Sunday that Evidon recently found 76 tracking programs on BarackObama.com,
and 40 trackers on MittRomney.com.
The prospect of data leakage via referrer headers has been known since at least 1999, when Internet pioneer Tim Berners-Lee warned of that possibility. More
recently, researchers from AT&T and Worcester Polytechnic Institute reported
that many popular sites and social networks, like Facebook and MySpace, were leaking personally identifiable data.
After
those reports came out, some sites revised the way they configured referrer headers.