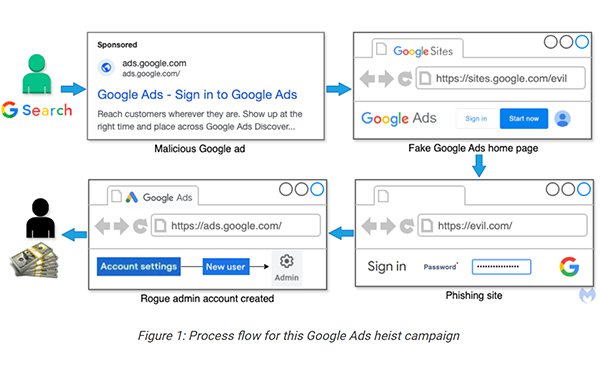
Online thieves are stealing as many advertiser accounts as
possible by impersonating Google Ads and redirecting victims to fake login pages.
They target individuals and businesses advertising in Google Ads by phishing for credentials. This means
stealing as many advertiser accounts as possible by impersonating Google Ads and redirecting victims to fake login pages.
Jerome Segura, senior director of research at Malwarebytes, identified
the hack. He believes the goal of the bandits is to resell those accounts on blackhat forums, while keeping some to themselves to perpetuate these campaigns.
Segura estimates this
malvertising operation likely affects thousands of Google Ads’ customers worldwide.
“We have been reporting new incidents around the clock and yet keep identifying new ones, even
at the time of publication,” he wrote in a blog post.
advertisement
advertisement
The fake Google Ads come from a variety of individuals and businesses in numerous locations. Some of those hacked accounts already
had hundreds of other legitimate ads running, and one of them was for a popular Taiwanese electronics company, he wrote in a blog post.
MalwareBytes first began to notice suspicious
activity related to Google accounts by accident, but after taking a deeper look were able to trace it back to malicious ads for Sponsored ads running on Google. They were specifically designed to
impersonate Google Ads.
The proof came after clicking on the three-dot menu meant to show more information about the advertiser. The same ad was found in different countries.
The
pages act as a gateway to external websites designed to steal usernames and passwords from the coveted advertisers’ Google accounts.
It’s all about phishing for Google account
credentials because after clicking on the “Start now” button found on the Google Sites page, the person is redirected to a different site that contains a phishing kit. JavaScript code
fingerprints users while they go through each step to ensure all important data is collected, he explains.
Analysts identified two groups of criminals running this scheme, but the more
prolific one comes from Portuguese speakers likely operating from Brazil.
Victims have also shared that they had received a notification from Google that also indicated suspicious logins
from Brazil.
The second group uses advertiser accounts from Hong Kong and appears to be based in Asia, perhaps originating from China.
A third campaign, not related to Google Ads,
relies on a fake CAPTCHA lure and heavy obfuscation of the phishing page. This malicious ad was for Google Authenticator.
Malwarebytes has since blocked all the ads found.