internet
New Worry: Covid-19 Scams That Carry Their Own Kind Of Viruses
- by P.J. Bednarski @pjbtweet, March 5, 2020
While the spread of
Covid-19 makes it once again urgent to be concerned about old-fashioned viruses, new data shows the more modern kind of virus — the computer kind — is having a field day, too.
A disquieting bulletin from cybersecurity software technology firm Check Point says that since January, its Threat Intelligence data has counted “over 4,000 coronavirus-related domains registered globally. Out of these websites, 3% were found to be malicious and an additional 5% are suspicious.”
The coronavirus spam and malware attempts are aimed at consumers and corporations that are trying to keep themselves one step ahead of the developing crisis, according to a Check Point spokesman.
The company says domains with a coronavirus theme are 50% more likely to be malicious than other domains registered during the same time frame. That includes domains with the word “Valentine” and “chocolate” that malware tricksters used on websites last month.
advertisement
advertisement
Check Point staffers say the incidence of these coronavirus malware sites is surprisingly high, compared to the average ones it monitors.
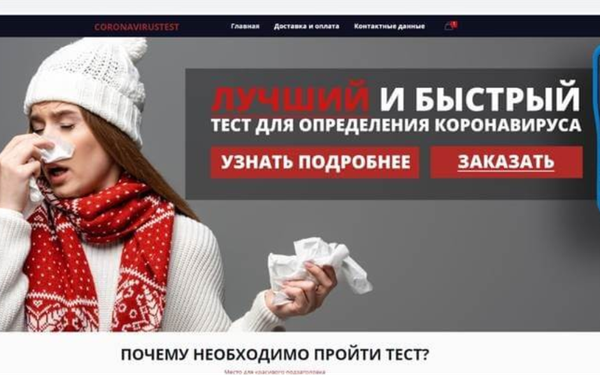
Many of the newly minted coronavirus domain names will be used by malware scammers to lure victims to their sites, or by entrepreneurs busily selling fake cures, vaccines or face masks, the company said. Its blog contained an example: a Russian ad for “the best and fastest test for coronavirus detection at the fantastic price of 19,000 Russian rubles [about US$300].” (See image above.)
Some of these sites might seem legitimate because they sprinkle in information purportedly from health officials or organizations that the worried public may find trustworthy. And right now, the public is understandably hungry for information.
Check Point noted another example: a widespread coronavirus-themed phishing campaign in Italy, where the Covid-19 crisis has been far more acute than it has so far in the United States.
The text cited a document supposedly prepared by the World Health Organization titled “Coronavirus: Important information about precautions.” Clicking on that document leads to the “download of Ostap Trojan-Downloader, which is known to be a Trickbot downloader,” says Check Point. That is described as a “dominant banking Trojan constantly being updated with new capabilities.”
The message was signed by Dr. Penelope Marchetti at the World Health Organization -- a nonexistent person, according to Check Point's investigation.
In January CheckPoint reported that at that time, scammers mainly picked on Japan, distributing malware called Emotet that pretended to be from a Japanese disability welfare service provider that explained where the the virus was said to be spreading in Japanese cities, and urging cam victims to open a document for more information. That document created an entry point for Emotet.
To protect against coronavirus-themed malware and phony-product domains, Check Point suggests some familiar safeguards, like looking for spelling errors or emails that contain logos that only almost look like the real one. Don’t click on promotional links in emails, and “Be cautious with emails and files received from unknown senders, especially if they prompt for a certain action you would not usually do.”


