Google Search continues to struggle with malicious
ads on its platform -- mostly from cybercriminals trying to trick people into downloading malware injected copies of free software applications.
One security expert talks about how large
language models and generative artificial intelligence could increase the risk.
The malicious ads typically appear above organic search results and often precede links to legitimate
sources of the same software.
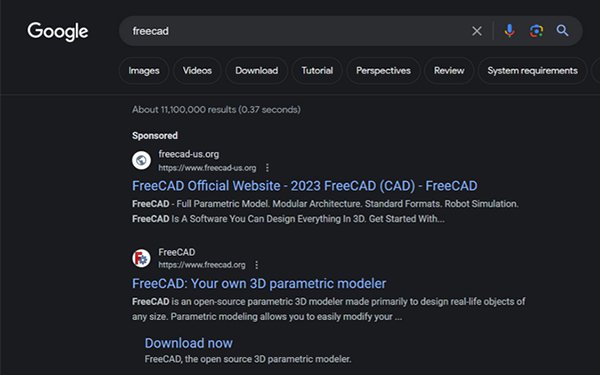
In late January, cybersecurity expert Brian Krebs found that a Google search for the free graphic design program FreeCAD returned results that show a
“Sponsored” ad at the top of the search results is advertising the software available from freecad-us[.]org.
Although this website claims to be the official FreeCAD website, it is
not. The result below the link is the legitimate freecad.org.
advertisement
advertisement
“I honestly think the day has long passed since it was safe to google for software downloads,” Robert Beckerdite,
director of Information Security at Vir Biotechnology, comments on the LinkedIn post. “Using reputable vendors and marketplaces still has risk but it's a lot safer. I would also suspect that
using [large language models] to find software is potentially risky because they are trained on what is on the internet.”
LLMs and GAI make it easier to information, including malware in
links to download software.
Vaidotas Sedys, head of risk management at Oxylabs, in an email acknowledged that Google has long had troubles with malicious advertising.
"Investigators have found that domains can be built up as legitimate for months, doing nothing bad, and then suddenly start spreading malicious ads,” he wrote in an email to MediaPost.
”This makes Google's job harder. They have recently updated their policy to make spreading malware through ads an egregious offense that triggers an immediate ban from advertising. What really
matters is how diligently they can enforce it."
Google is not the only platform to experience ad injection lately, says security expert Casey Rauth. He wrote in a post on LinkedIn that he has
seen plenty of unusual Facebook ads in the timeline feed.
Krebs, which publishes a blog post called KrebsOnSecurity, verified the malicious site through a review at DomainTools.com, which
shows the domain was registered on January 19, 2024. It is one of more than 200 domains on the internet with a name that is confusingly similar to popular software titles.
These
malicious sites, he wrote in a blog post, also steal content from information sources such as Gartner, PCWorld, and TechRadar.
Tom Hegel, principal threat researcher at the security
firm Sentinel One, told Krebs that he has been tracking these domains for more than a year.
He said these seemingly benign software download sites will sometimes "turn evil, swapping
out legitimate copies of popular software titles with back-doored versions that will allow cybercriminals to remotely commander the systems."
The sites use automation to pull in fake content.
Then they rotate in and out of hosting malware. Sometimes the malicious downloads are only offered to visitors who come from specific geographic locations, such as the United States.
This
group for one ad campaign would wait until the domains gained legitimacy on the search engines, flip the page and then flip it back, meaning that one day it would have malicious code and the next it
would not.
Krebs pointed to a report that Hegel co-authored in February 2023, which outlines the same network Sentinel One named MalVirt. It explains how the surge in malicious ads
spoofing various software products was directly responsible for a surge in malware infections from infostealer trojans like IcedID, Redline Stealer, Formbook, and AuroraStealer.
The
spike in malicious software type ads "came not long after Microsoft started blocking by default Office macros in documents downloaded from the Internet," Krebs wrote.
Maintaining a safe advertising ecosystem and keeping malware off of its platforms is a priority for Google.
A spokesperson told Krebs that "bad actors often employ sophisticated measures to
conceal their identities and evade our policies and enforcement, sometimes showing Google one thing and users something else. We'e reviewed the ads in question, removed those that violated our
policies, and suspended the associated accounts. We'll continue to monitor and apply our protections.”