Malwarebytes researcher Jerome Segura and SEO strategist Elie
Berreby have come across a new phishing campaign targeting search engine optimization (SEO) professionals with malicious Semrush Google Ads that aim to steal their Google account credentials.
The researchers believe the bad actors are after Google Ads accounts that would enable them to create new malvertising campaigns.
The operation is going after Semrush's visibility
management software as a service platform that offers SEO, advertising, and market research, according to the blog post. The platform reportedly serves 40% of Fortune 500 companies and 117,000 paying customers.
advertisement
advertisement
Researchers explain
how the fraudsters are "taking an indirect approach to hacking Google advertisers and by the same token likely gaining access to Semrush accounts."
Malwarebytes in January
documented a large phishing campaign targeting
Google accounts via Google Ads.
The company now believes the group has now regrouped and transitioned to a malicious ad scheme for Google Ads that redirects to a fraudulent login page for
Semrush.
"While the phishing page uses the Semrush brand, only the 'Log in with Google' option is enabled, forcing victims to authenticate with their Google account username and password," the
researchers wrote in the blog post.
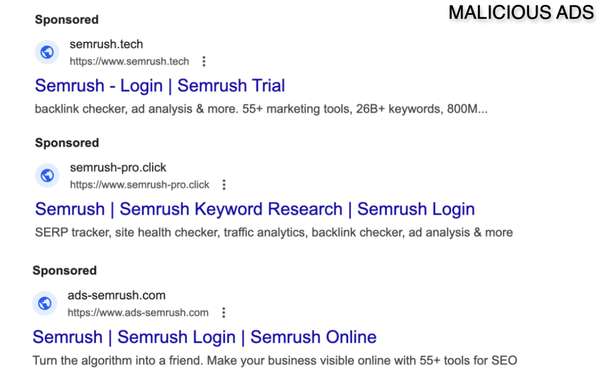
The researchers observed the transition. The campaign soon after began to take shape with Google ads now fully moving away from the “Google
Ads” brand to impersonate Semrush.
The domain names registered are all variations on the Semrush name. Each ad, however, uses a unique domain name that redirects to more static domains
dedicated to the fake Semrush and Google account login pages.
Something to keep in mind, according to the post, is that Google Analytics and Google Search Console can contain critical and
confidential information for a business, and can reveal details on website performance, user behavioral patterns, and strategic focuses.
This would provide access to a businesses' raw data
and could include name, phone, business name, address, email and the last 4 digits of a Visa card.