An ad-fraud operation called SlopAds discovered by Human's
Satori Threat Intelligence team was disrupted after 224 malicious applications on Google Play were used to generate 2.3 billion ad requests daily.
The fraud campaign is a bit unusual
because in “many fraud campaigns, we see threat actors create and use custom tooling for things like determining whether to do fraud or hiding the campaign from
discovery,” Lindsay Kaye, vice president of Threat Intelligence for Human Security, wrote in an email to MediaPost. “In SlopAds, this is the first
time we saw a threat actor use an existing, normally benign tool designed for marketing attribution in this way.”
In terms of sophistication, he wrote, it’s an interesting example
of a threat actor seeing how to use this existing tool in part of their campaign that might go unnoticed more easily than a custom utility.
advertisement
advertisement
Human, a cybersecurity company, found that the apps
were downloaded more than 38 million times from 228 countries. The operation used obfuscation, which makes something more difficult to understand, and steganography, a technique used to hide
information. These tools were used to conceal malicious behavior from Google and security tools.
The highest percentage of ad impressions of the 2.3 billion bid requests occurred in the United
States -- 30%, followed by India at 10% and Brazil at 7%.
Google removed all identified apps listed in the report from Google Play, and protected users with Google Play Protect, which warns
users and blocks apps known to exhibit SlopAds associated behavior when the app is installed on Android devices.
The research team initially identified anomalies in its data that indicated
possible invalid traffic (IVT). In this case, the anomalies were related to some specific apps that eventually turned out to be part of a larger threat, SlopAds.
The ad fraud contained
multiple levels to avoid being detected by Google's app review process and security software. For example, if a user installed a SlopAd app through the Play Store, without coming from one of the
campaign's ads, it would act as a normal app, performing the proper functions.
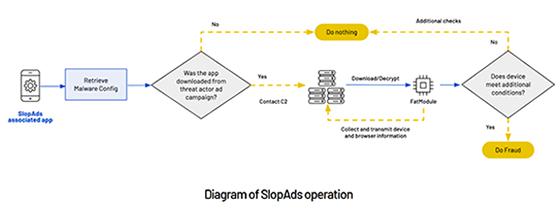
If the app was installed by a user’s click by arriving through one of the threat actor's ad campaigns, the
software used Firebase Remote Config to download an encrypted configuration file that contained ad fraud malware module. The app would then determine if it was installed on a legitimate user's device,
rather than being analyzed by a researcher or security software.
Passing these checks meant it downloaded four PNG images that used steganography to conceal pieces of malicious files used
to run the ad fraud campaign.
Once downloaded, the images were decrypted and reassembled on the device to form the complete "FatModule" malware, which was used to conduct the ad fraud.
Domains impersonated game and new sites, serving ads continuously through hidden WebView screens to generate more than 2 billion fraudulent ad impressions and clicks daily.
Fraud
campaigns have increasingly become sophisticated, according to the report. When asked how advertisers can protect their
companies, Kaye pointed to pushing “their DSP and SSP partners to incorporate supply quality signals that go beyond GIVT and SIVT filtration.”