DoubleVerify Thursday announced the discovery
of ViperBot, described by the company as “a sophisticated advertising fraud scheme that attempts to steal over $8 million each month in ad spend” across connected television (CTV) and
mobile video.
Mark Zagorski, CEO at DoubleVerify, called ViperBot "one of the most sophisticated fraud schemes" the company has identified.
DoubleVerify said its clients are
protected from the scheme, but the code continues to spoof more than five million devices and up to 85 million ad requests daily. The company identified ViperBot in Q4 2021. Its peak activity
occurred during the busy holiday season between Q4 2021 and Q1 2022. During this time, there were spikes.
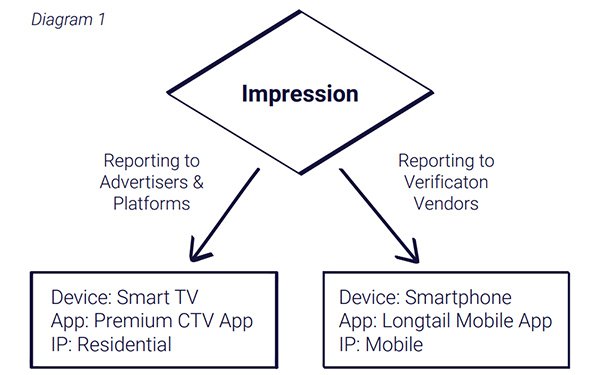
Here’s how it works: ViperBot strips the code that verifies ad impressions from
providers like Oracle, Integral Ad Science (IAS) and Pixalate, and then conceals and redirects the code through real devices to hide the fraudulent
activity in an attempt to go undetected.
advertisement
advertisement
ViperBot relies on verification stripping, the removal of verification tags set by providers, and a new tactic, discovered by DoubleVerify called
verification redirection.
Now fraudsters not only remove verification tags from the ad being delivered, but also reinsert them inside of cheap ad slots running on real devices in an attempt to
prevent detection, making it difficult for measurement providers to recognize fraudulent activity.
DoubleVerify’s technology powers DV Fraud Lab, a dedicated team of data scientists,
mathematicians and analysts from the cyber-fraud prevention community. The Fraud Lab relies on a variety of approaches to detect fraud, from AI and machine learning to manual review.
Last
month, DoubleVerify reported that CTV fraud schemes cost publishers $144
million in 2021, identifying three schemes in late 2020 and one in early 2021 that cost publishers between $1 million and $5 million a month.